Installing Software Vulnerability Manager CentOS
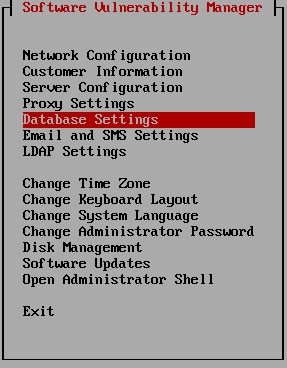
The following steps appear in the order that they appear in the installation procedure. You can use the arrow and Page Up/Down keys to navigate, press ESC to go back or F2 to open an administrator shell.
| • | Initial Configuration |
| • | Network Configuration |
| • | Customer Information |
| • | Server Configuration |
| • | Disk Initialization |
| • | Database Configuration |
| • | Proxy Configuration |
| • | Email and SMS Settings |
| • | Software Updates |
| • | LDAP Configuration |