Specifying Control Access via Active Directory
AdminStudio 2024 R2 | 28.0 | ThinApp Assistant
You can control the access of users to a ThinApp application by specifying Active Directory groups on the General Settings page. At build-time, ThinApp assigns a unique GUID-like number to uniquely identify each Active Directory Group that you identify. Members of those groups will have access to the ThinApp application. For more detailed information about how Active Directory permissions are assigned, see About Controlling Access to ThinApp Applications.
To specify control access via Active Directory on the General Settings page, perform the following steps:
To specify control access via Active Directory:
| 1. | In the ThinApp Assistant, open the General Settings page. |
| 2. | Select the Control Access via Active Directory option. The fields below are enabled. |
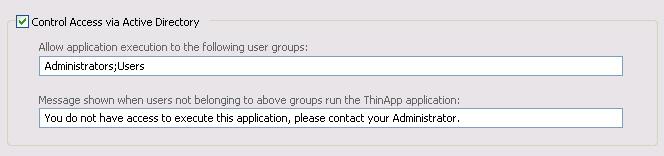
GroupOne;GroupTwo;GroupThree
| 4. | In the Message shown when users not belonging to above groups run the ThinApp application, enter the message that will be displayed when users that do not belong to the specified groups attempt to launch a ThinApp application. |
Caution:If you do not select the Control Access via Active Directory option, anyone who has access to a directory containing a ThinApp application will be able to run the application.
About Controlling Access to ThinApp Applications
Note the following about controlling access to ThinApp applications via Active Directory:
| • | You must be connected—You must be connected to your Active Directory domain when you build the ThinApp application. |
| • | Groups must exist—The Active Directory groups that you specify must exist when the ThinApp application is built. |
| • | If you delete a group and then recreate it, you must rebuild—If you delete a group and recreate it, you will need to rebuild the ThinApp application in order to authenticate against the “new” group. |
| • | Offline users can authenticate using cached credentials—When users are offline, they can authenticate using cached credentials. Assuming that the user can log into their laptop, ThinApp Active Directory authentication will still work. |
| • | Sometimes you may need to update credentials manually—Cached credentials may not refresh on clients until the next Active Directory refresh cycle. To manually refresh the cached group policy credentials, you can use the gpupdate command. Sometimes the user may need to log-off before the credentials are recached. |
| • | “Administrators” and “Everyone” Groups use same credentials—Special groups like Administrators and Everyone have the same SID on every Active Directory domain and Workgroup. Other groups you create will have a domain-specific SID, meaning a user cannot create their own local group with the same name to bypass authentication. |