App Portal / App Broker for ServiceNow 2016 | Settings > Single Sign On
In previous releases, access to the App Portal app store was limited to domain-authenticated users only. Starting with App Portal, 2016, you can configure single sign-on authentication for your users, enabling them to access the App Portal app store on-the-go from locations outside the corporate network or VPN.
Important • Single sign-on authentication is not supported when using the App Portal mobile interface.
Single sign-on is configured on the Site Management > Settings > Single Sign On view:

Site Management > Settings > Single Sign-On View
App Portal 2016 provides support for the following single sign-on authentication types:
| • | SAML 2.0—SAML (Security Assertion Markup Language) 2.0 is an XML-based, open-standard data format for enabling web browser single sign-on. |
| • | OAuth 2.0—OAuth is an open standard for authorization, commonly used as a way for users to log in to third party websites using their Google, Facebook, Microsoft, Twitter, etc. accounts without exposing their password. |
| • | OpenID—OpenID is an open standard and decentralized authentication protocol which allows users to be authenticated by co-operating sites (known as relying parties) using a third-party service. |
| • | Custom—To implement a custom single sign-on authentication type, you would need to write a custom SSL page (.aspx) to redirect to. App Portal is installed with a boilerplate custom SSL page named CustomSignon.aspx, which your services team can customize for your organization. |
Important • When using single sign-on, App Portal needs to be configured to run with anonymous authentication in IIS. By default, Windows Authentication is selected.
The Single Sign-On view includes the following properties:
|
Single Sign-On Type |
Field |
Description |
|
SAML 2.0 |
Identity provider certificate |
Click Browse select the authentication certificate that you obtained from your identity provider platform. |
|
Single sign-on URL |
Enter the URL that you obtained from your identity provider platform. |
|
|
Signature node XPath |
The default setting is //ds:Signature. Adjust this signature node XPath as needed, per your identity provider platform. |
|
|
Attribute node XPath |
The default setting is below. Adjust this attribute node XPath as needed, per your identity provider platform. /saml2p:Response/saml2:Assertion/saml2:Subject/saml2:NameID |
|
|
OpenID Connect |
Single sign-on URL |
Enter the URL that you obtained from your identity provider platform. |
|
Authentication request end point |
Enter the URL that you obtained from your identity provider platform. |
|
|
Client ID |
Enter the client ID that you obtained from your identity provider platform. |
|
|
Redirect URL |
Enter the following: http://YOURAPPPORTALSERVER/esd/OpenIdSignOn.aspx |
|
|
State |
Enter any value that will passed back to App Portal by the identity provider platform post login for validation. The State value helps to validate that the correct ID Token is received. Also, this value comes as a Key in the Form element. |
|
|
Nonce |
Enter any value that will passed back to App Portal by the identity provider platform post login for validation. The Nonce value helps to validate that the correct ID Token is received. Also, it is used to mitigate replay attacks. |
|
|
Bypass Token Validation |
When the client application receives the ID Token from the identity provider platform, it is the responsibility of the client to validate the ID Token. This validation process involves a number of steps which would get performed when the Bypass token validation option is not selected. If you want to bypass token validation, select the Bypass token validation option. |
|
|
Generate “Initiate Login URL” |
Click to generate a URL based upon the entered information. Copy this URL, return to the account settings page of your identity provider platform and paste this URL into the Initiate login URL field. |
|
|
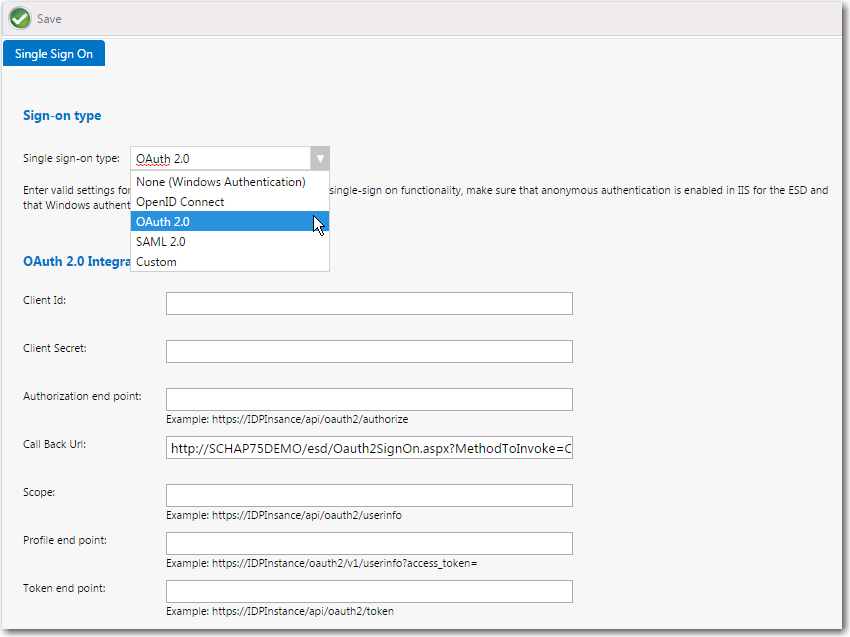
OAuth 2.0 |
Client Id |
Enter the ID provided by your identity provider platform. |
|
Client Secret |
Enter the “client secret” provided by your identity provider platform. |
|
|
Authorization end point |
Enter URL provided by your identity provider platform. |
|
|
Call back Url |
Enter the following URL: http://YOURAPPPORTALSERVER/esd/oauth2SignOn.aspx?MethodToInvoke=CallBack |
|
|
Scope |
Enter URL provided by your identity provider platform. |
|
|
Profile end point |
Enter URL provided by your identity provider platform. |
|
|
Token end point |
Enter URL provided by your identity provider platform. |
|
|
Custom |
Single sign-on URL |
When you select this option, the settings defined in your custom SSL page are displayed. |
See Also
Configuring Corporate Single Sign On
Configuring SAML 2.0 Authentication
Configuring OAuth 2.0 Authentication
Configuring OpenID Connect Authentication
Configuring Custom Authentication
App Portal / App Broker for ServiceNow 2016 Administration Guide09 August 2016 |
Copyright Information | Flexera Software |