Scanning
Software Vulnerability Manager 2019 (Cloud Edition)
Software Vulnerability Manager 2019 allows scanning of target hosts using the following approaches:
|
•
|
Single Host Agent-based scans are conducted by the Software Vulnerability Manager 2019 Agent that can be installed in different modes: Single Host mode, Network Appliance mode, or Command Line mode. |
|
•
|
Alternatively, you can scan the target hosts by launching a scan from the system where the Software Vulnerability Manager 2019 console is running. By using this approach, no software is installed in the target hosts. The scanning is performed using standard operating system services. This scan is also referred to as a “remote scan”. |
The various types of scan are listed and shown below:
Below is a visual overview of the Software Vulnerability Manager 2019 scanning options:
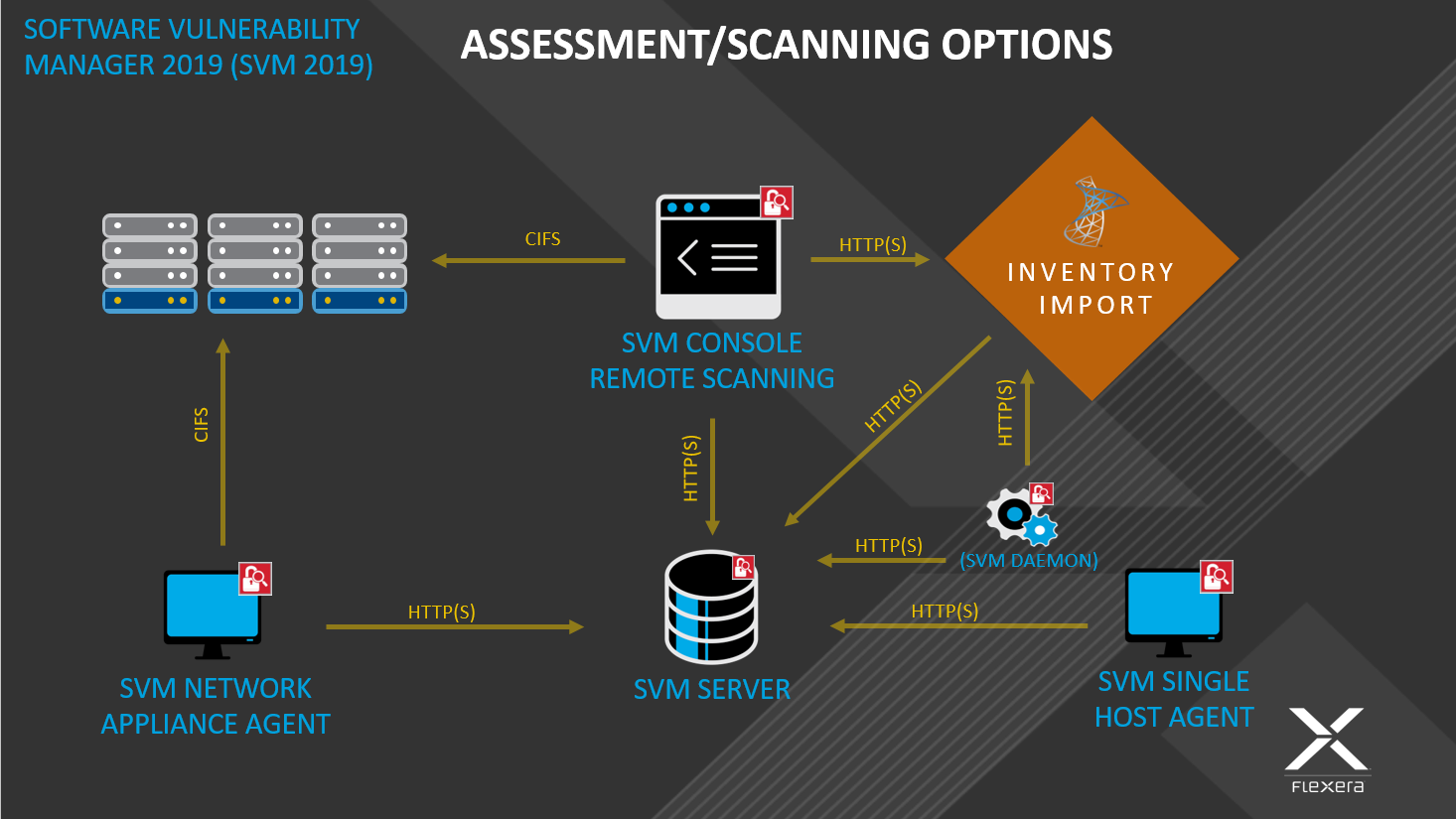
Note • If the WSUS Self-Signed Certificate will be used to sign the update packages created by Software Vulnerability Manager 2019, you can use a different certificate as an alternative.
Important • Administrators must ensure that Software Vulnerability Manager 2019, and its scanning Agent respectively, have access to all necessary system and online resources which allow the application to run as intended. The following addresses should be white-listed in the Firewall/Proxy configuration to ensure that the client system is allowed access to these online resources: crl.verisign.net, crl.thawte.com, http://*.ws.symantec.com, and https://*.secunia.com/
Open topic with navigation
Software Vulnerability Manager (Cloud Edition)
2019

