Step 2 - Certificate Status
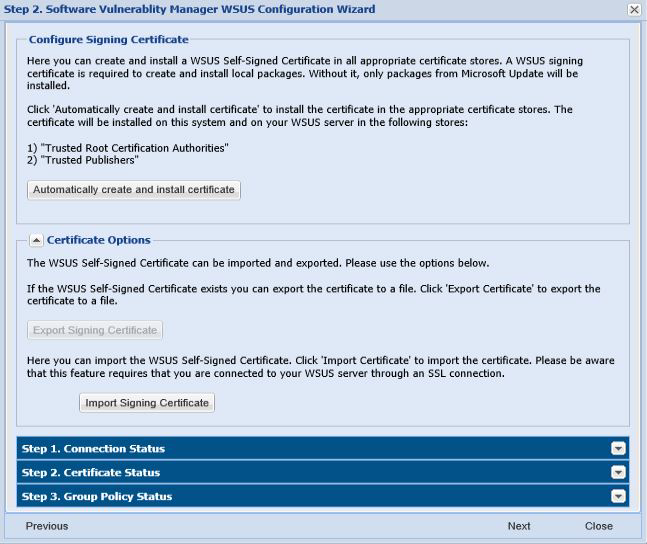
A code-signing certificate is needed to publish third-party updates to WSUS/System Center so they can be deployed as patches. In this Step Software Vulnerability Manager can request the WSUS to create and install the WSUS Self-Signed Certificate.
To create and install a WSUS Self-Signed Certificate in all appropriate certificate stores, click Automatically create and install certificate.
The WSUS Self-Signing Certificate must be installed/provisioned in the following systems:
| • | WSUS Server |
The system running Software Vulnerability Manager (note that the certificate must also be installed on the system running the Software Vulnerability Manager console)
| • | Clients receiving the Update |
The created certificate is required and it will be used for all future publishing. Without it, only packages from Microsoft Update will be installed.
If you would like to use your own CA certificate instead of the Microsoft WSUS Self-Signing Certificate, click Import Signing Certificate.
At Step 3 – Group Policy Status, the certificate created/imported in this step will be provisioned to all clients through a GPO.
Important:Be careful not to re-provision a signing certificate on a WSUS server that already has a signing certificate assigned. Doing so can cause issues with certificate validation at the WSUS server and target computers unless BOTH certificates (new and old) are left in the appropriate certificates stores (Trusted Publishers and Trusted Root Authorities). It can also cause issues with troubleshooting.
Once a certificate is either inserted or created it does not need to be re-created until it expires or needs to be replaced.
Click Automatically create and install certificate. The certificate will be installed on the WSUS server in the following stores:
| • | Trusted Root Certification Authorities |
| • | Trusted Publishers |
| • | WSUS – The certificate in this location must also contain the private key |
Expand the Certificate Options to access the import and export certificate features.