Passing Groups Memberships in the SAML 2.0 Assertion
Important:
To pass group memberships in the SAML 2.0 assertion, you must have the Administrative privileges in your organization’s identity provider and one of the following Flexera One roles: Manage organization or Administer organization. For complete descriptions of each role available in Flexera One, see Flexera One Roles.
Group memberships for each user are passed from the IdP to Flexera One in the SAML 2.0 assertion which Flexera One accepts to log the user in. The “groups” attribute statement must include the name of each Flexera One group to which the user should be added.
Here is an example of a SAML 2.0 attribute statement which specifies the user should be added to the Admins and Billing groups:
...
<saml2:Attribute Name="groups" NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:unspecified">
<saml2:AttributeValue">Admins</saml2:AttributeValue>
<saml2:AttributeValue">Billing</saml2:AttributeValue>
</saml2:Attribute>
...
The following sections provide detail on how to setup the groups attribute for common IdPs.
Configure Okta to Send the Groups Attribute
To configure Okta to send the Groups attribute
|
1.
|
In the Okta Administrator UI, go to the Flexera One app. |
|
2.
|
On the General tab, in the SAML Settings section, select Edit. |
|
3.
|
Click Next to reach the Configure SAML step. |
|
4.
|
Configure the profile claims and Group Attribute Statements as shown in the following: |
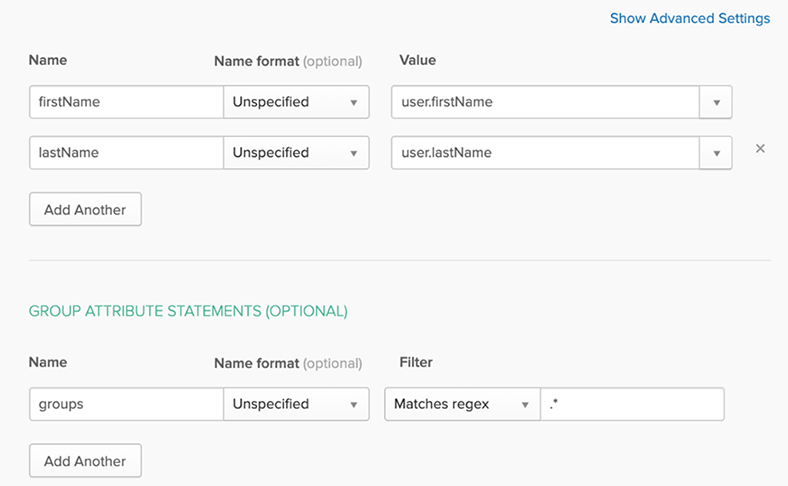
Note:Choose any desired filter to limit the groups that will be synchronized to Flexera One. Use the Matches regex = .* filter to send all Okta group memberships.
|
5.
|
Click Next and then Finish. |
Configure Azure Active Directory (AD) to Send the Groups Attribute
This section provides procedures to configure Azure AD to send the Groups attribute.
To configure Azure Active Directory to send the Groups attribute
|
1.
|
In the Azure AD Administrator UI, go to Enterprise applications and select the application setup for Flexera One. |
|
2.
|
From the Manage section in the left nav, select Single sign-on. |
|
3.
|
In the User Attributes & Claims section, select Edit. |
|
4.
|
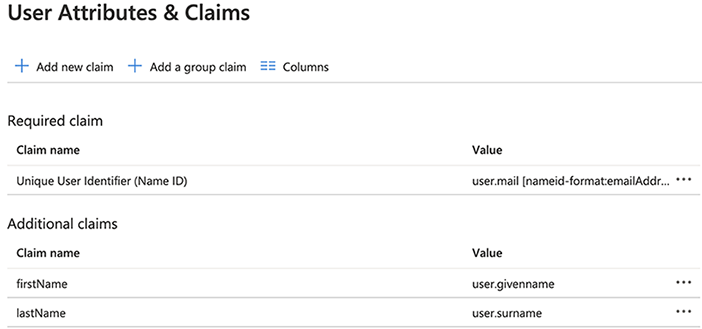
Click Add new claim to add the following attributes: |
|
•
|
firstName: user.givenname |
|
•
|
lastName: user.surname. |
Important:Do not populate the optional Namespace field for any of the claims.
|
5.
|
Click Add a group claim and do the following: |
|
a.
|
Select which groups should be returned in the claim. |
Important:For Azure group claims, we recommend that you select only groups assigned to the Azure application and not select All Groups because this can cause an issue in larger environments (for example, if a user has over 100 groups).
|
c.
|
Use the custom name groups for the attribute. |
|
d.
|
Do not populate the optional Namespace field for the groups claim. |
Note on the Azure AD Groups Claim
Azure AD may be limited to only exporting group IDs (Object Ids, for example: "999038b9-c966-9qc3-b49e-988847fayywe9") but not group names.
|
•
|
Flexera One’s group name must match the Azure AD group ID. |
|
•
|
Flexera One’s group description field may be used to store the friendly name of the group. |
For example, the following group configurations would map correctly:
Azure AD Group
|
•
|
GroupID—"999038b9-c966-9qc3-b49e-988847fayywe9" |
Flexera One Group
|
•
|
Name—"999038b9-c966-9qc3-b49e-988847fayywe9" |
|
•
|
Description—"Billing Dept". |
For example, the following group configurations would not map correctly:
Azure AD Group
|
•
|
GroupID—"999038b9-c966-9qc3-b49e-988847fayywe9" |
Flexera One Group
|
•
|
Description—"Billing related permissions". |

