How Credentials are Used
| • | Multi-Tenent Credentials |
| • | Matching Credentials to Policies |
For policies that reach out to external systems to gather information or take actions, the policy author should use credentials for authenticated API calls. When such a policy is applied by a policy manager, they will select which credential in the current account to use when the policy runs.
By default, the credential selector shows only those credentials that match the credential provider specified in the policy template. For details, see Matching Credentials to Policies. The user can click the View all credentials link to instead show all credentials in the system that match the schemes defined in the policy template.
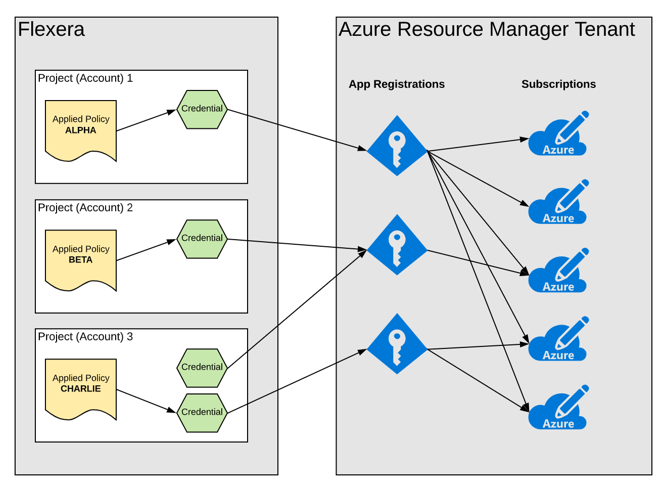
Depending on the design of the policy and the type of credential being used, a policy may interact with more than one service account/tenant/subscription/project. For example, when any Flexera-built policy (see List of Flexera Policies) for Azure and Google is applied, it iterates through all available subscriptions/projects that the credential has access to.
Therefore, when creating the credentials in the provider system, remember that when you register that credential in Flexera, any account that has that credential will run policies against all the tenants it has access to. The following diagram illustrates this behavior using Azure as an example. Note that this scenario is not possible with AWS as a separate credential is needed for each AWS account -- this is a limitation of how AWS has designed cross-account roles.
In the following example:
| • | Policy Alpha will run against all 5 subscriptions. |
| • | Policy Beta will run against only the 1 subscription. |
| • | Users in Project 3 will have the choice to use either credential when applying a policy. In this example, Policy Charlie will run against 2 subscriptions. |
Note:This multi-tenant behavior depends on the design/code of the policy template itself. All Flexera-built policies contain code to identify all tenants the credential has access to and run the policy against each. To replicate this behavior, inspect and replicate the code of a Flexera-built policy.
Matching Credentials to Policies
To simplify the user experience around applying policies, the system provides a mechanism to match credentials in the system with the credential-selector when applying a policy. The match is performed by inspecting the tags in the policy template credential declaration. The default format for provider-specific credentials, like Azure Resource Group Manager, uses a key of provider and value of the provider name and is passed in the body using the following format: "tags": [{"key":"provider","value":"azure_rm"}]. The expected format for all provider-specific credentials is documented in Provider-Specific Credentials. More information on credential matching for policy templates can be found on the Retrieving Data page in the Authorization section.