Configuring Single Sign-On (SSO)
Note:The following information is unique to the single sign-on vendor Okta (SAML 2.0). Single sign-on procedures from other vendors may vary.
To set up Okta (SAML 2.0) to use as a single sign-on (SSO) with Software Vulnerability Research:
|
2.
|
Create an admin account. |
|
3.
|
Click Create New App to create a new Okta SSO app. |

|
4.
|
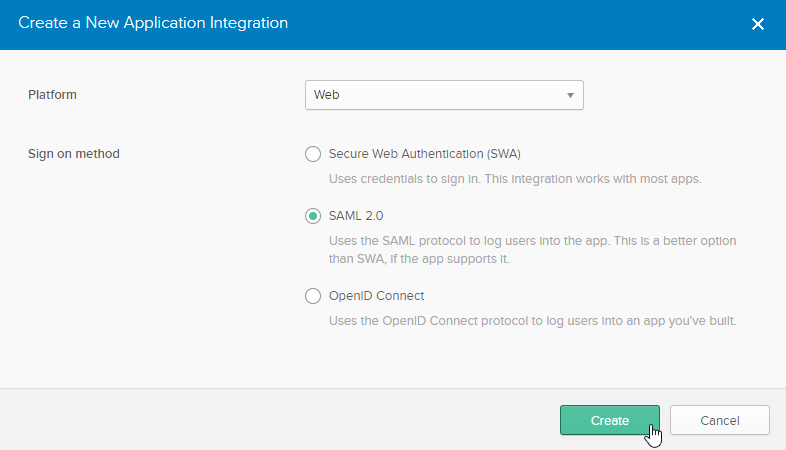
Choose Web for the Platform and SAML 2.0 for the Sign on method. Then click Create. |
|
5.
|
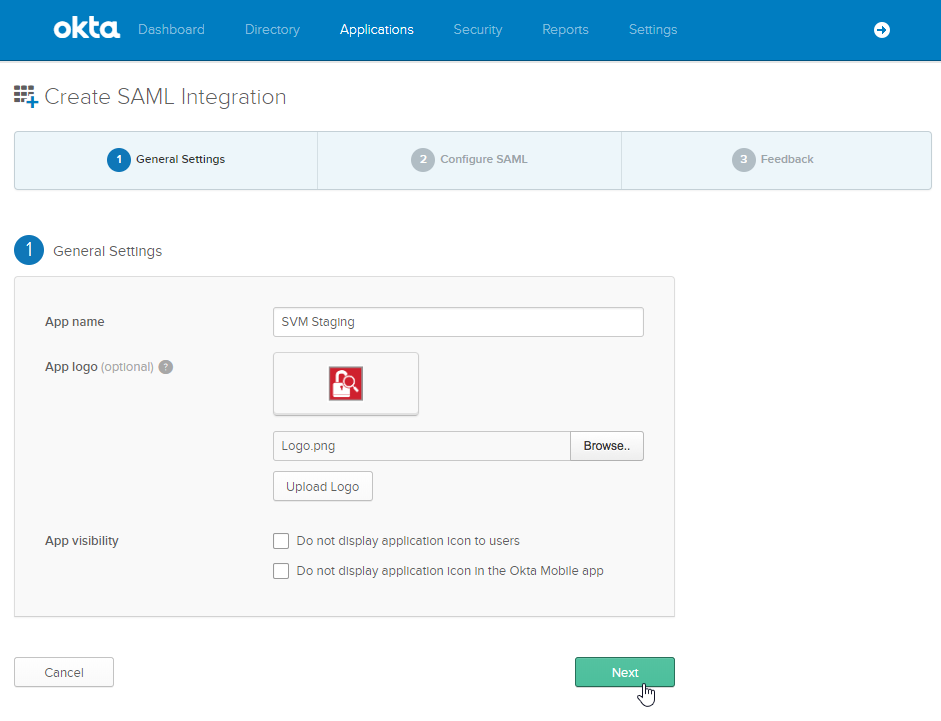
Enter an App name (Example: SVM) and App logo (Example: see Software Vulnerability Research logo below). Then click Next. |
|
6.
|
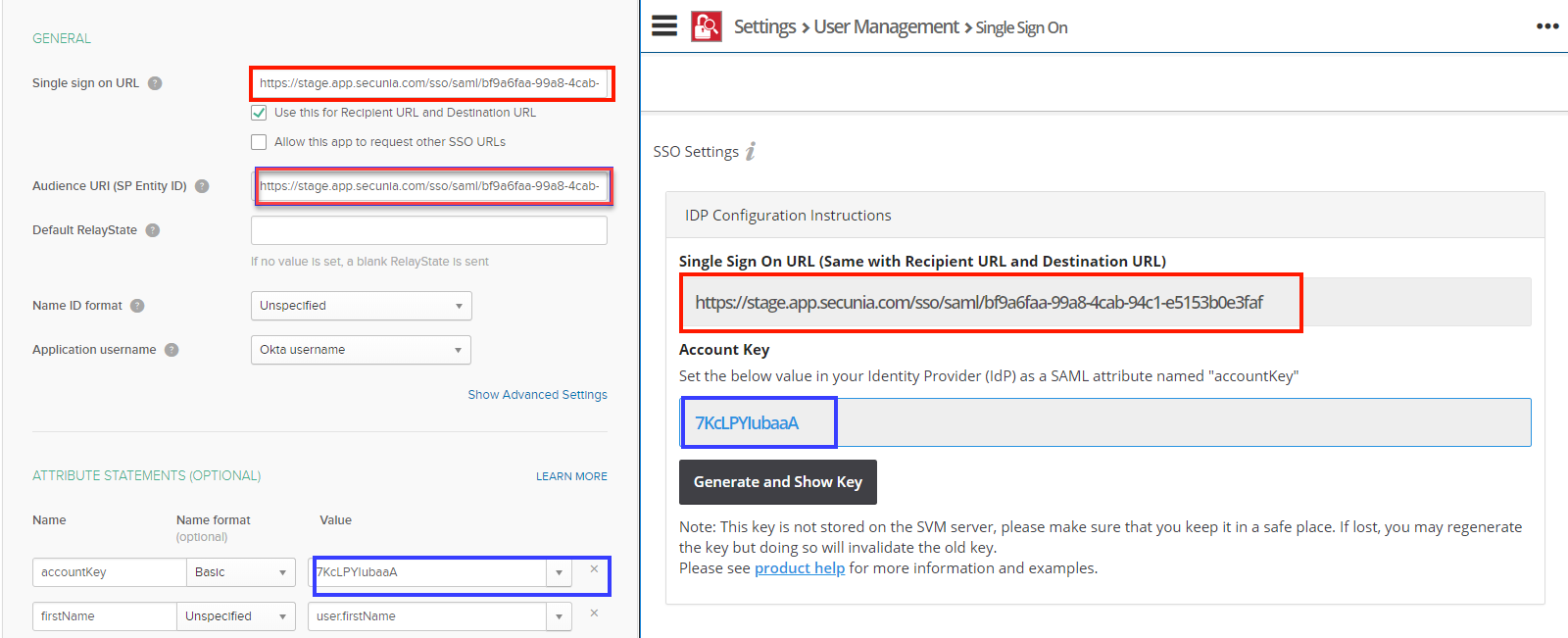
Copy the following from the Software Vulnerability Research Settings > User Management > Single Sign On fields and paste in the Okta SAML Settings > fields: |
|
•
|
Single Sign On URL (Same with Recipient URL and Destination URL) to Single sign on URL and Audience URL (SP Entity ID) |
|
•
|
Account Key to accountKey Value |
Complete the remaining Okta SAML Settings > Attribute Statements (Optional) name and value fields using the field’s drop-down list:
|
7.
|
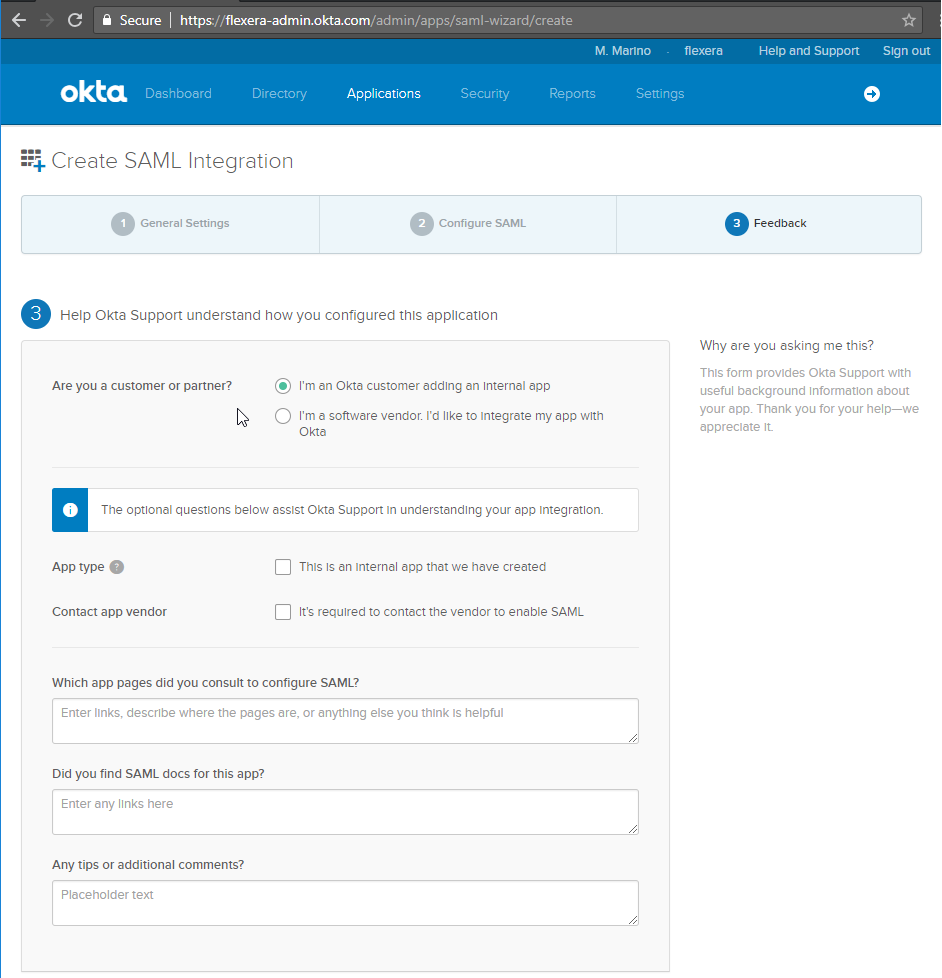
Click (if not already selected) I’m an Okta customer adding an internal app for the Create SAML Integration - Step 3 Feedback screen. You can leave the rest of the fields blank. |
|
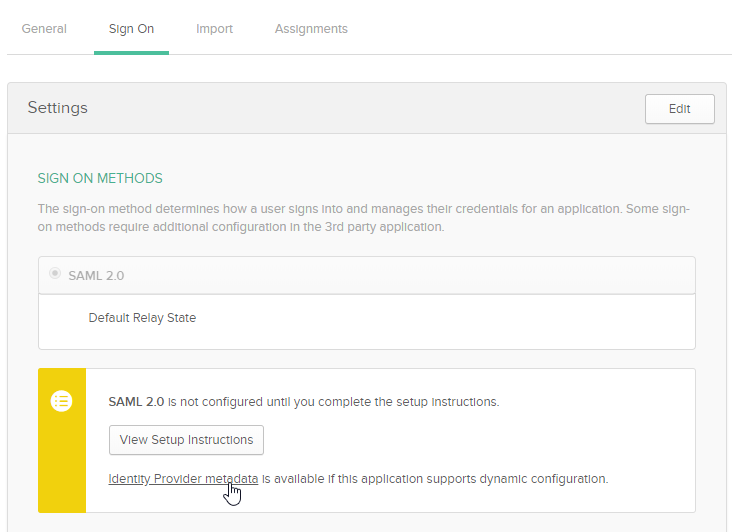
8.
|
At the Okta Sign On Settings screen, click the Identity Provider metadata link. |
|
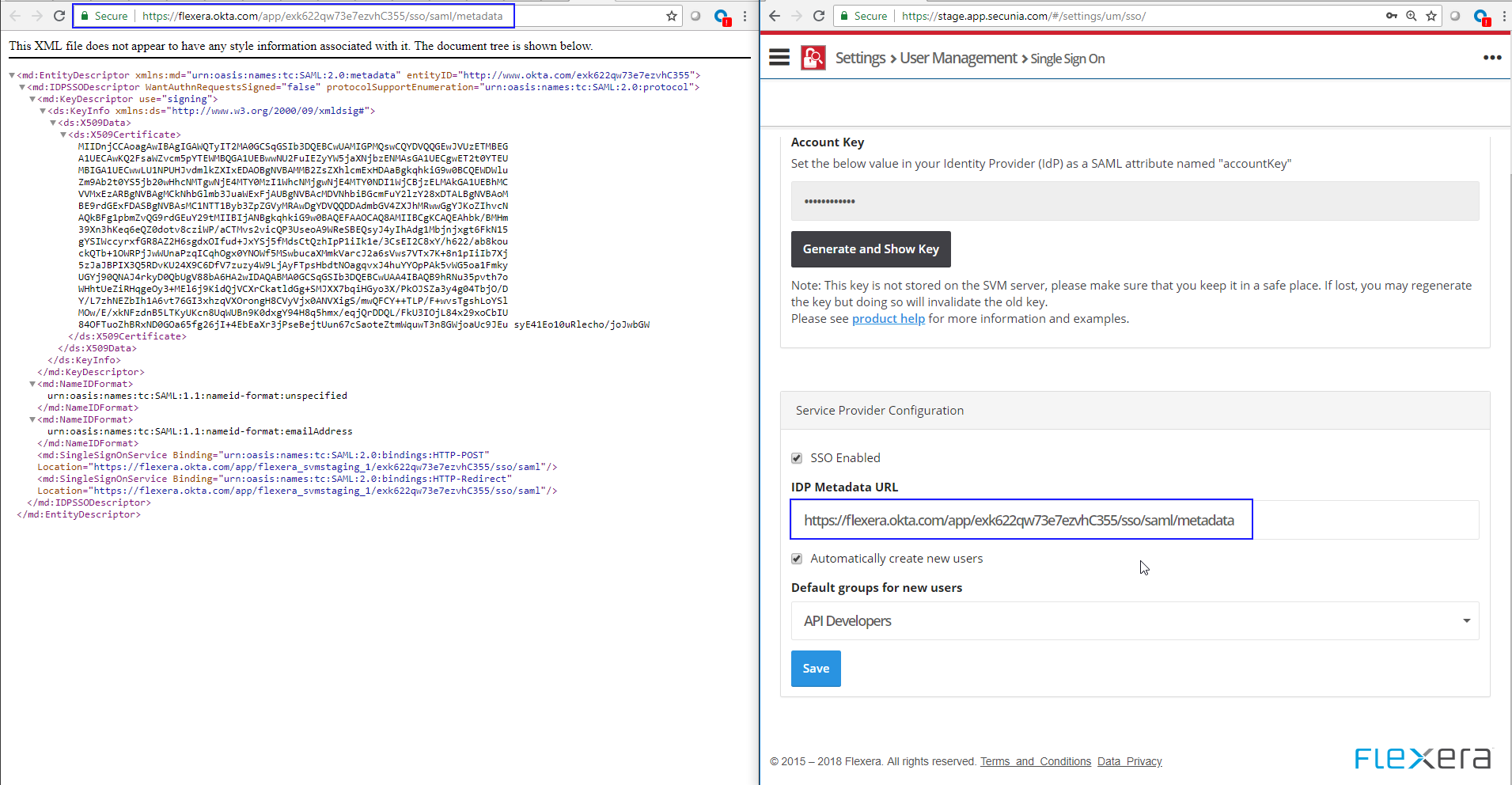
9.
|
Copy the Identity Provider metadata URL from Okta into the Software Vulnerability Research Settings > User Management > Single Sign On > IDP Metadata URL field. Check SSO Enabled, check Automatically create new users, and assign a Default group for new users. |
Note:For a secure connection, the Assertions Signed (or similarly named) setting should be enabled on your IDP.
|
10.
|
If you want to disable standard login options for all of your users (except root), select the Disable standard login option under Settings > User Management > SSO Settings > Service Provider Configuration. |
|
11.
|
Click Save to on the Settings > User Management page. |
Important:Before selecting this option, make sure that SSO is working correctly, to prevent user lockout.
|
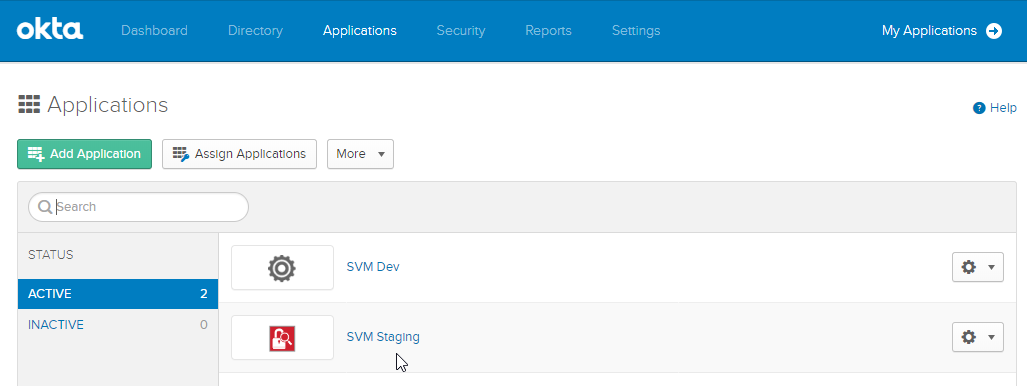
12.
|
Add Software Vulnerability Research users to the Okta SSO account. |
|
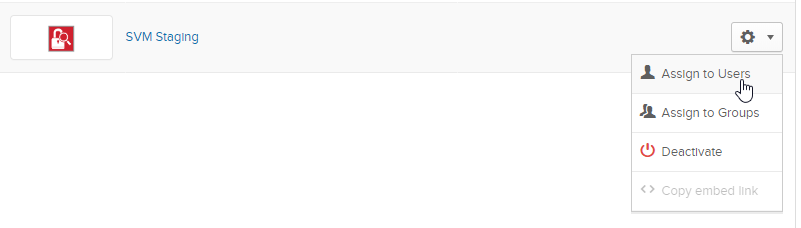
13.
|
Assign Software Vulnerability Research users to the Okta SSO app. A reset password link is sent to each user. |
|
14.
|
Users open the reset password link, reset their password, and click open the Okta SSO application. |
|
15.
|
Users are then logged into the Software Vulnerability Research Login page. |
Important:For security purposes, Software Vulnerability Research has a session timeout that will log you off after 2 hours of inactivity.









